a byte of ICSI, May 2015
the monthly newsletter of
International Computer
Science Institute
Recent Seminars
DARPA Research and Program Priorities
William Regli
DARPA
Thursday, May 14, 2015
10:00 a.m., Conference Room 6A
Probabilistic Modeling of Speech and Language
Zhijian Ou
Tsinghua University, Beijing, China
Tuesday, May 12, 2015
12:30 p.m., Conference Room 5A
Inside the Cookie Jar: Measuring the Use of Cookies in the Wild
Roberto Gonzalez
NEC Labs Europe
Thursday, May 7, 2015
4:00 p.m., ICSI Lecture Hall
Natural Language Understanding for Application-Specific Domains
Sean Trott
ICSI
Tuesday, April 28, 2015
12:30 p.m., Conference Room 5A
Quantifying Similarity in Bird Calls
Naomi Harte
ICSI & Trinity College Dublin, Ireland
Tuesday, April 21, 2015
12:30 p.m., Conference Room 5A
Uncharted Lecture Series: Using Artificial Intelligence to Protect Privacy
Michael Tschantz
ICSI
Thursday, April 16, 2015
4:00 p.m., ICSI Lecture Hall
in the press
"I think a future direction is getting inside these systems and understanding where possible cases of discrimination are happening."
See full list of press coverage.
ICYMI:
Networking and Security researcher Mark Allman gave the keynote address at the Passive and Active Measurement Conference, held in New York, New York on March 19 and 20. His address was titled “Towards Better Internet Empiricalism."
What We're Writing
K. Thomas, E. Bursztein, N. Jagpal, M. Abu Rajab, N. Provos, P. Pearce, G. Ho, D. McCoy, C. Grier, V. Paxson, A. Nappa, and A. Kapravelos. Ad Injection at Scale: Assessing Deceptive Advertisement Modifications. Proceedings of the 36th IEEE Symposium on Security and Privacy, San Jose, California, May 2015
N. Vallina-Rodriguez, S. Sundaresan, C. Kreibich, N. Weaver, and V. Paxson. Beyond the Radio: Illuminating the Higher Layers of Mobile Networks. Proceedings of the International Conference on Mobile Systems, Applications, and Services (MobiSys 2015), Florence, Italy. Also appeared as ICSI Technical Report TR-14-003, December 2014, May 2015
R. Rasti, M. Murthy, N. Weaver, and V. Paxson. Temporal Lensing and its Application in Pulsing Denial-of-Service Attacks. Proceedings of the 36th IEEE Symposium on Security and Privacy, San Jose, California, May 2015
D. G. Anderson, S. S. Du, M. W. Mahoney, C. Melgaard, K. Wu, and M. Gu. Spectral Gap Error Bounds for Improving CUR Matrix Decomposition and the Nystrom Method. Proceedings of the 18th International Conference on Artificial Intelligence and Statistics (AI & Statistics 2015), San Diego, California, May 2015
I. Castro, A. Panda, B. Raghavan, S. Shenker, and S. Gorinsky. Route Bazaar: Automatic Interdomain Contract Negotiation. Proceedings of the 15th Workshop on Hot Topics in Operating Systems (HotOS XV), Kartause Ittingen, Switzerland, May 2015
The Great Cannon - Another Tool in China’s Censorship Box
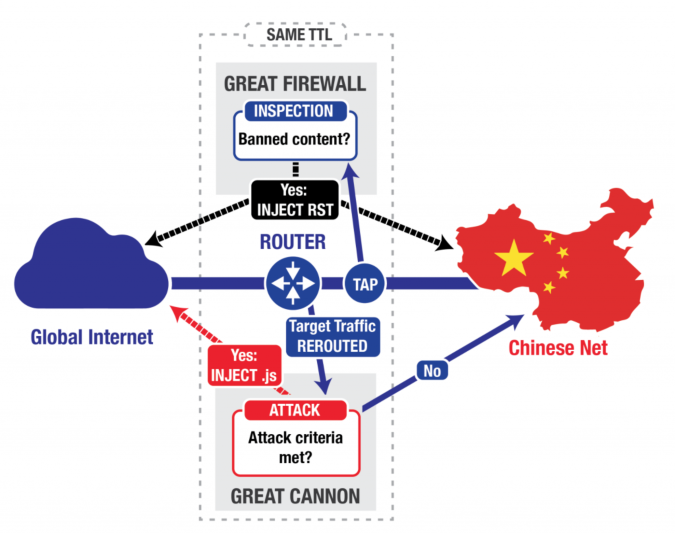 The Chinese government appears to have used distributed denial-of-service attacks against a nonprofit organization, GreatFire.org, that helps Chinese users circumvent the administration’s Internet censorship regime, according to a report by the Citizen Lab at the University of Toronto’s Munk School of Global Affairs that ICSI researchers collaborated on. While the Chinese administration has long censored the Internet by using a tool known as the Great Firewall to block traffic to certain web sites, the new system works offensively by redirecting traffic to attack targets.
The Chinese government appears to have used distributed denial-of-service attacks against a nonprofit organization, GreatFire.org, that helps Chinese users circumvent the administration’s Internet censorship regime, according to a report by the Citizen Lab at the University of Toronto’s Munk School of Global Affairs that ICSI researchers collaborated on. While the Chinese administration has long censored the Internet by using a tool known as the Great Firewall to block traffic to certain web sites, the new system works offensively by redirecting traffic to attack targets.
The researchers say that the tool, which they have named the Great Cannon, was responsible for a flood of Internet traffic on March 16 that nearly crashed servers rented from Amazon Web Services by GreatFire to provide mirror images of blocked sites. On March 26, a similar attack was directed at GitHub pages run by GreatFire.org. At its height, the attack was racking up $30,000 a day in bandwidth fees from Amazon, according to GreatFire’s blog. GitHub called the attack on its repositories the largest distributed denial of service attack in its history.
"This is very much an escalation."
Bill Marczak in
“China Deploys New Weapon for Online Censorship in Form of ‘Great Cannon’”
April 10, 2015, Andrea Peterson, The Washington Post

Sylvia Ratnasamy Wins ACM Grace Murray Hopper Award
Professor Sylvia Ratnasamy is the winner of the 2014 ACM Grace Murray Hopper Award, given each year to an outstanding young computer professional. Ratnasamy, a senior Networking and Security researcher as well as an assistant professor of computer science at UC Berkeley, is recognized for her contributions to the first efficient design for distributed hash tables, a critical element in large-scale distributed and peer-to-peer computing systems. ACM cited Ratnasamy’s 2001 paper, “A Scalable, Content-Addressable Network,” which she co-wrote while a graduate student with fellow members of ACIRI, the precursor of ICSI’s Networking and Security Group. The paper is the seventh most cited in the area of networks and communications, according to Microsoft Academic Search.Read more.
What's Next
upcoming seminars
Sonia Chiasson is the Canada Research Chair in Human Oriented Computer Security and a faculty member in the School of Computer Science at Carleton University in Ottawa, Canada.
Understanding Users' (In)Secure Behaviour
Wednesday, May 20, 2015
2:00 p.m., ICSI Lecture Hall

Elisabeth Wehling is a postdoctoral fellow in the AI Group, funded by the Federal Ministry of Education and Research (BMBF) through the FITweltweit program, administered by the German Academic Exchange Service (DAAD).
A Nation Under Joint Custody: How Conflicting Family Models Explain Conservatism and Liberalism
Thursday, May 21, 2015
4:00 p.m., ICSI Lecture Hall

Nelson Morgan is a speech researcher and the former director of ICSI as well as a professor in residence emeritus at UC Berkeley. He led the speech research effort at ICSI from 1988 through 2012.
Are Learned Features Enough for Robust DNNs? A Question of Nature vs. Nurture
Thursday, May 28, 2015
4:00 p.m., ICSI Lecture Hall
Who's Visiting
- Martha Larson, Audio and Multimedia, Visiting Researcher, Delft University of Technology, Netherlands (03/26 - 9/15)
- Manfred Eppe, Artificial Intelligence, DAAD Postdoc (4/13/2015 - 03/31/2016)
- Marco Caselli, Networking and Security, Graduate Student at the University of Twente, Netherlands (04/20 - 7/25)
- Fred Roosta, Research Initiatives, Postdoc (arrived 4/30)
- Marian Harbach, Networking and Security, DAAD Postdoc (5/1/2015 - 10/31/2016)
- Antonia Scatton, AI, Visiting Researcher, Reframe America (5/1 - 7/31)
- Vadim Shapiro, Research Initiatives, Visiting Researcher, University of Wisconsin (5/1 - 7/31)
Check out our redesigned pages
We’ve redesigned the web page for our visiting program and added a page listing potential mentors of visiting scholars.

